- CyberVade's Weekly Scoop 🍦
- Posts
- No. 6 | CyberVade's Weekly Scoop 🍦
No. 6 | CyberVade's Weekly Scoop 🍦
Bankspoofing, is cybersecurity an effective introvert?, learn about network security and vCSO
Hi there, this is CyberVade’s Weekly Scoop🍦, where we bring you Cybersecurity, AI, Data Privacy and Compliance knowledge updates.
Every issue, we’ll take you on a tour of the latest cybersecurity headlines (⚡️), throw in some witty analysis (🧠 ), serve up a mini cybersecurity MBA - because who doesn’t love a byte-sized brain boost? (🎓) And finally, shine a spotlight on one of CyberVade’s solutions to show how it can save the day ( 🚀).
In today’s edition, we’ve got the following for you:
⚡️Bankspoofing, and a vulnerability was discovered so old it could drive 🚗
In the Netherlands, citizens are falling victim to scammers imitating to be their bank, using the registered bank telephone number - a practice called “Bankspoofing”, of which banks have said that it isn’t possible. Read about it here.
An 18 year old vulnerability has been discovered that affects all major browsers including Chrome, Firefox, and Safari. The consequence? Hackers can access local services and gain unauthorized access, potentially leading to data breaches and remote code execution. Article can be accessed here.
🧠 Cybersecurity: an effective introvert?
The cybersecurity industry is like the world's most effective introvert: massive, important, and quietly ruling everything from the background.
You probably don’t think about it much, and the only thing you know about cybersecurity might be your spam folder or the McAfee antivirus pop-up you keep clicking away. For example, have you ever heard of Palo Alto Networks? Maybe not.. but don’t worry, you’re not alone. If you’re not in the cybersecurity industry, chances are this name won’t mean much to you.
However, this company is a titan in cybersecurity, with a market capitalization1 of $109 billion. To put that in perspective, that's more than Hyundai, Ford, and Kia combined. Yes, the people who make the cars you actually recognize and possibly drive.

CyberVade analysis on market capitalization. Source: Yahoo Finance, Companiesmarketcap.com
Using a Google Trend Analysis as a proxy for how frequently these companies are on peoples’ mind, it becomes clear how relatively unknown Palo Alto Networks actually is. So maybe Cybersecurity really is the most effective introvert.
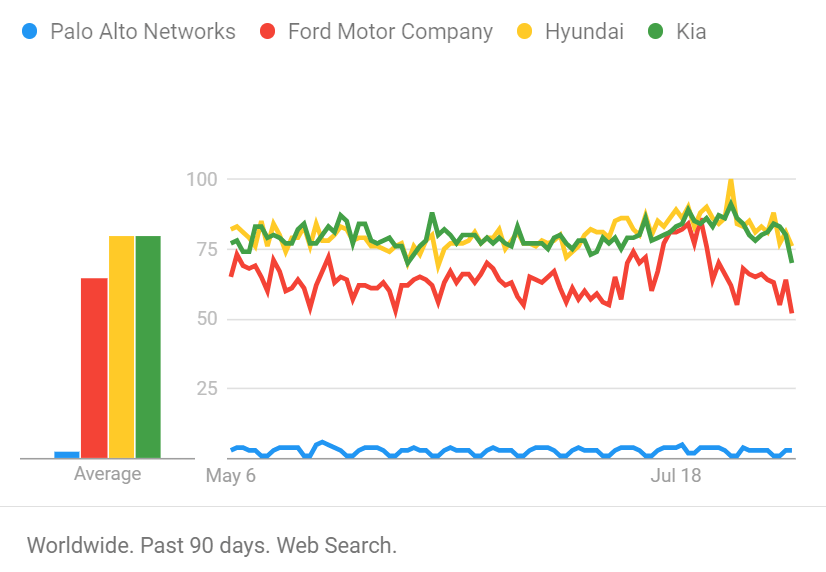
CyberVade analysis on Google Trends
🎓 Network Security and Architecture
Welcome Cybersecurity 101. In this mini MBA series we distill essential cybersecurity knowledge into quick, digestible lessons 🍪 .
Think of it as a crash course in keeping your digital world safe, without the lengthy lectures. Today’s course: Network Security and Architecture.
—
🎯Actionable Takeaways:
Implement- and Invest in Secure Network Architecture
Align Security with Business Strategy
Foster a Security-First Culture
—
Network security and architecture are foundational to protecting modern digital systems.
Network architecture: the design and layout of an organization's computer network. It includes the physical hardware, logical design, and protocols that facilitate communication and resource sharing within and outside the network.
Network security: encompasses the policies, practices, and technologies used to safeguard the integrity, confidentiality, and availability of data as it traverses the network. It involves protecting the network from unauthorized access, misuse, malfunction, modification, and destruction.
CORE CONCEPTS | DESCRIPTION |
|---|---|
Defense in depth | layers multiple security measures to protect the network. This might include firewalls, intrusion detection systems (IDS), encryption, and secure access controls at different points in the network |
Segmentation | dividing the network into segments to contain breaches. For example, critical systems may be isolated in a secure zone with strict access controls, while less sensitive areas of the network are in separate segments. |
Zero Trust Architecture (ZTA) | Access is denied (not trusted) by default and only granted when required, based on prior verification and approval, even within the network perimeter. This approach minimizes the attack surface by ensuring that every request for access is authenticated and authorized. |
Network Monitoring | Continuous monitoring helps detect and respond to anomalies and potential threats in real-time. Such monitoring increasingly makes use of AI to identify anomalies in network behavior. |
🚀 vCSO - virtual Chief Security Officer
In "Solution Spotlight” we highlight the CyberVade solutions protecting your data from cyber villains. Each edition introduces a new solution making waves, breaking down its features and benefits. Whether you're a pro or just starting, meet the tech superheroes keeping your digital world safe!
Virtual Chief Security Officer
A vCSO is an excellent way for organizations that recognize the importance of professional cybersecurity oversight and strategy and wish to take action, not only to implement tools, but to build a cybersecure organization - without having the budget for a dedicated FTE. Leveraging a vCSO brings you the skills and expertise, at a fraction of the cost.
CyberVade’s vCSO approach is based on a client-centric and pragmatic approach to bring you results. The extend of the scope is agreed-upon with the clients and typically includes setting strategic objectives, architecture review, risk assessments/threat analysis, threat modelling, risk detection scope, (regulatory) standard selection and compliance approach, cybersecurity stack review and adjustments, process and procedures monitoring, and more. Pragmatic as we are, the first 90 days will be used to perform risk analysis, create a roadmap and to build the foundation to transform your organization’s cybersecurity framework to become increasingly cybersecure.
1 Market Capitalization = [Company Share Price] x [Number of Outstanding Shares]
